73% of Modernizations Fail. Here's a Guide to Avoiding the Common Traps.
Ignoring your legacy system isn’t a strategy—it’s a decision to let technical debt silently drain your budget. The “if it ain’t broke, don’t fix it” argument ignores a critical fact: in terms of security, talent availability, and operational drag, it’s already broken.
Legacy system modernization isn’t an IT expense. It’s a capital investment to stop a predictable, compounding financial leak.
The Real Costs of Legacy System Inertia
The belief that delaying modernization saves money is a common but flawed assumption. Data indicates that maintaining legacy systems actively diverts capital from innovation to operational triage. The financial drain is multifaceted and predictable.
Maintenance costs can consume up to 80% of IT budgets in certain industries. For context, the U.S. government allocates $337 million annually to operate just ten of its oldest systems. This isn’t a static problem; it’s an accelerating one. As talent pools for languages like COBOL shrink, the costs and risks compound.
The Growing Skills Gap and Its Financial Impact
A primary cost driver is human capital. The number of developers proficient in COBOL, Fortran, or PL/I is decreasing. Consequently, their compensation rates are increasing.
The average age of a COBOL programmer is over 55. This isn’t just a staffing issue; it’s a significant business risk. Sourcing a qualified COBOL developer can cost 50-75% more than hiring for a modern stack like Java or Python.
This skills gap translates directly to financial impact:
- Longer Mean Time to Resolution (MTTR): Fewer available experts mean critical bug fixes can take weeks instead of days, increasing system vulnerability and business disruption.
- Increased Project Risk: Modifying brittle, poorly documented code without deep institutional knowledge significantly increases the probability of introducing critical failures.
- Recruitment Costs: Companies are forced into bidding wars for a diminishing talent pool.
Security Vulnerabilities and Technical Debt
Legacy systems were architected before the modern threat landscape existed. They often lack fundamental security protocols, making them high-value targets. Each day a system goes unpatched represents a calculated risk of a data breach, which can result in millions in regulatory fines and reputational damage.
Simultaneously, technical debt—the implied cost of rework caused by choosing an easy solution now instead of using a better approach that would take longer—compounds. A feature request that requires hours in a modern microservices architecture could demand weeks in a monolithic system due to code entanglement. This is a direct, measurable cost of inaction.
This is why a legacy system risk assessment is a mandatory first step. It quantifies these hidden liabilities and builds the business case for investment.
Legacy System Risk Profile
To justify modernization, you must quantify the risks of maintaining the status quo. This table translates technical risks into business impacts suitable for a CFO-level discussion.
| Risk Category | Description | Potential Business Impact |
|---|---|---|
| Operational Risk | Frequent outages, slow performance, and inability to integrate with modern SaaS tools. System instability leads to business disruption. | $500K - $2M+ per hour of downtime for critical systems. Lost sales, SLA penalties, and decreased employee productivity. |
| Security Risk | Outdated security protocols, unpatched vulnerabilities, and lack of support from original vendors. A prime target for data breaches. | Average cost of a data breach is $4.45M. Fines (GDPR, CCPA), reputational damage, and loss of customer trust. |
| Talent & Skill Gap Risk | Dwindling pool of developers proficient in legacy languages (COBOL, Fortran). High cost and long lead times to hire or retain talent. | 50-75% higher recruitment costs than for modern developers. Project delays and inability to innovate due to lack of skills. |
| Compliance Risk | Inability to meet modern regulatory requirements (e.g., GDPR data portability, PCI DSS). Manual workarounds are error-prone and costly. | Fines up to 4% of global annual revenue for non-compliance. Legal fees and mandatory operational overhauls. |
| Technical Debt | The compounding cost of rework. Simple changes take weeks due to complex, brittle code, hindering agility and speed to market. | 40% of developer time spent on bad code and tech debt. Slower feature releases, lost competitive advantage. |
Each risk represents a quantifiable financial liability. The sum often demonstrates that the cost of inaction far exceeds the cost of a modernization initiative.
Choosing Your Modernization Path
Deciding to modernize is the first step. The next is selecting the right strategy. This decision will define the organization’s agility, cost structure, and competitive position for the next decade.
Maintaining a legacy system is a predictable path of budget drain and innovation atrophy. Modernization presents a path toward growth.
This flowchart illustrates a critical point: inaction is an active choice to allocate funds to maintenance over value creation. Here are the primary modernization options.
Re-host: The “Lift-and-Shift” Method
Re-hosting involves moving an application from on-premise servers to a cloud infrastructure provider (IaaS) like AWS, Azure, or GCP with minimal to no code modification.
- When to consider it: This is the appropriate strategy for rapid data center evacuation due to lease expiration or a corporate mandate to exit physical hardware. It is the fastest path to cloud infrastructure.
- When NOT to buy: If an application performs poorly on-premise, it will perform poorly and expensively in the cloud. This approach moves problems without solving them and often results in higher operational costs due to unoptimized resource consumption.
Re-platform: The “Lift-and-Tinker”
Re-platforming involves moving an application to the cloud while making minor modifications to leverage cloud-native services. A common example is migrating a self-managed Oracle database to a managed service like Amazon RDS.
This strategy allows for incremental adoption of cloud benefits without a full rewrite. The primary risk is introducing new dependencies into a monolithic codebase, where small changes can have unintended consequences. Rigorous regression testing is non-negotiable.
Re-factor and Re-architect: The Deconstruction
This is where the most significant value is unlocked. Re-factoring involves restructuring existing code for improved efficiency and maintainability without altering its external behavior. Re-architecting is a more substantial undertaking, typically involving the decomposition of a monolithic application into microservices.
A frequent mistake is attempting a “big bang” re-architecture. These projects have a high failure rate due to their complexity and long duration. By the time the project is complete, the original business requirements have often changed.
A lower-risk alternative is the Strangler Fig Pattern. New functionality is built as independent microservices that interface with the legacy system. Over time, these services incrementally replace and “strangle” the monolith’s functionality until it can be decommissioned. This approach delivers value iteratively and reduces risk. It is also the point where a decision is made between building on existing foundations or starting new, a topic covered in our guide on Brownfield vs. Greenfield modernization.
Replace: The Full “Rip-and-Replace”
In some cases, a legacy system is so outdated, brittle, or misaligned with business strategy that the only logical path is to decommission it entirely. It is replaced with a new solution, often a commercial off-the-shelf (COTS) or SaaS product.
This is often the most disruptive and capital-intensive option upfront. However, if the legacy system actively constrains the business or presents unacceptable risk, replacement can yield the highest long-term ROI. The business case must demonstrate that the cost of the status quo is greater than the cost of replacement.
Any modernization effort must align with the organization’s broader digital transformation strategy guide, not exist as an isolated IT project.
The demand for these services is clear. The legacy modernization market, valued at $15-25 billion, is projected to reach $45-75 billion by 2033. Service providers currently hold a 58% market share, a testament to the specialized skills required. Cloud-native re-architecting, with a 22.74% CAGR, is the fastest-growing segment.
How to Vet a Modernization Partner
Selecting the right implementation partner is a critical decision. The difference between a true technical partner and a sales-driven vendor can result in millions in budget overruns and project delays. Vetting requires a skeptical, tactical approach to get beyond marketing materials and uncover proven capabilities.
The objective is not to find a vendor who agrees with everything, but one that demonstrates a deep understanding of common failure patterns in complex migrations.
Beyond the Sales Pitch
Initial vendor conversations are designed to build confidence; your role is to test for substance. You must drive the conversation toward the difficult but necessary topics: cost models, failure analysis, and deep technical specialization.
Demand specifics on pricing. Vague responses are a red flag. An experienced partner can provide range-bound estimates tied to specific metrics.
For a COBOL to Java/C# migration, a credible cost estimate should fall between $1.50 and $4.00 per Line of Code (LOC). A vendor unable to provide a similar metric-driven range for your specific project likely lacks sufficient historical data from comparable engagements.
The price itself is less important than the methodology used to derive it. Transparent, experience-based pricing is a non-negotiable requirement.
Probing for Deep Technical Specialization
Most vendors claim to have “experts,” but expertise in legacy modernization is highly specific. A team skilled in greenfield cloud-native development may have no experience with the data-level complexities of a mainframe migration. Your questions must be precise enough to expose these gaps.
Here are direct questions to probe for technical depth:
- For Mainframe Migrations: “Describe a project where you handled COBOL COMP-3 (packed decimal) to Java
BigDecimalconversion. What specific data validation and reconciliation tools did you use to guarantee no decimal precision loss?” - For Database Modernization: “Walk me through your strategy for migrating a database with 20+ years of historical data while maintaining zero downtime for the live system. What specific tools do you prefer for Change Data Capture (CDC)?”
- For Re-architecting to Microservices: “Explain how you identify service boundaries within a monolith. What quantitative data do you use to defend your ‘seams’ and prove you aren’t just creating a distributed monolith?”
An experienced engineer will answer with specific patterns, tool names, and project anecdotes. A salesperson will revert to high-level marketing language.
Analyzing Past Failures and Client References
Any vendor claiming a perfect project record is either inexperienced or dishonest. Failure is an inherent part of complex engineering. The key is how they analyze and learn from it.
Ask directly: “Tell me about a modernization project that went significantly over budget or schedule. What was the root cause, and what specific process changes did you implement as a result?” The answer reveals more about their accountability and process maturity than any success story.
When checking references, ask tactical questions:
- What was the final cost overrun compared to the initial statement of work?
- How did the partner’s core technical team respond when they encountered a significant, unforeseen architectural challenge?
- Were there any surprise performance or data integrity issues post-launch?
- Would you re-hire the exact same technical team for a future project?
The final question addresses the common “bait-and-switch” tactic where a vendor sells their A-team but staffs the project with junior resources.
Finding the right partner is a critical process. For a broader market perspective, you can explore comparisons of top IT consulting companies to evaluate different firms.
Vendor Evaluation Matrix
Use a structured matrix to move beyond subjective impressions and focus on tangible evidence of competence.
| Evaluation Criteria | Red Flag Example | Green Flag Example |
|---|---|---|
| Technical Specialization | Vague claims of “cloud expertise” without specific legacy system experience. | Provides case studies on migrating your exact tech stack (e.g., AS/400 to Azure). |
| Cost Transparency | Refuses to provide a per-unit cost range (e.g., per LOC, per server). | Offers a clear cost model like “$1.50-$4.00 per LOC” with defined variables. |
| Failure Analysis | ”We’ve never had a project fail.” | Openly discusses a past failure, the root cause, and the process changes it prompted. |
| Team Composition | Unable to name the specific senior architects who will be on your project. | Introduces you to the lead architect during the vetting process. |
| Data Migration Strategy | ”We use standard ETL tools.” | Describes a multi-phased approach with automated data reconciliation and parallel runs. |
| ”When Not to Buy” Guidance | Pushes their solution for every problem. | Advises against modernization if a system is stable and the ROI is not compelling. |
Choosing a modernization partner is fundamentally a risk-mitigation exercise. You are looking for the team that has already made expensive mistakes with someone else’s budget and has the hardened processes to prove they learned from them.
Common Failure Points in Modernization Projects
A high percentage of legacy modernization projects fail to meet their objectives. Failure is rarely a single catastrophic event but rather a series of predictable technical and organizational missteps.
This isn’t about assigning blame; it’s about acknowledging that these are high-risk initiatives. The institutional inertia of “if it ain’t broke, don’t fix it” is a powerful counterforce. A recent survey found that 62% of organizations still operate legacy software, and 50% defer upgrades simply because the old system remains functional. This creates a feedback loop where investment is delayed until a crisis occurs. You can review the full survey findings on modernization delays here.
The Lure of the ‘Big Bang’ Rewrite
The “big bang” rewrite—replacing an entire system in one monolithic project—is a seductive but extremely high-risk strategy. Executives are often drawn to its perceived finality.
It almost always fails.
The scale is unmanageable. Over a typical 18-36 month timeline, business requirements change, key personnel depart, and market conditions shift. The new system is often partially obsolete upon launch.
An incremental approach like the Strangler Fig Pattern is a more prudent strategy. New services are built around the monolith, gradually replacing functionality piece by piece. Big bang projects create unacceptable risk; incremental rewrites build momentum and deliver continuous value.
Technical Pitfalls in the Weeds
Small technical errors can have cascading, catastrophic effects, leading to data corruption or performance degradation that silently undermines the project.
- Data Precision Loss: This is a common failure when migrating from mainframe environments. COBOL’s
COMP-3(packed decimal) data type uses fixed-point arithmetic, essential for financial calculations. Migrating this data to a standard Java floating-point primitive can introduce minute rounding errors that become significant over millions of transactions. The correct approach is to use a library like Java’sBigDecimal, but this detail is often overlooked. - Creating a ‘Distributed Monolith’: In the pursuit of microservices, teams often define service boundaries incorrectly. If the new “microservices” require constant, synchronous communication with each other to perform a single business function, the result is not a resilient, decoupled architecture. It is a distributed monolith, which has all the operational complexity of a distributed system with none of the benefits.
Organizational and Cultural Failures
Technical challenges are often more straightforward to solve than organizational dysfunction. Modernization projects are frequently derailed by politics, inertia, and a lack of executive commitment.
The most common non-technical failure is the lack of a true executive sponsor. This requires more than just budget approval; it requires a C-level champion who understands the strategic rationale and will defend the project against competing priorities and budget cuts.
Another common failure is underestimating change management. A new system alters established workflows. Without early user involvement, comprehensive training, and active management of the human transition, user adoption will fail. A technically perfect system that no one uses is a failed investment.
How Do You Know If You Actually Succeeded?
A successful deployment is not the same as a successful project. If a modernization initiative does not deliver tangible business value, you have simply replaced one expensive system with another.
Success is not measured by IT-centric vanity metrics like “lines of code migrated” or “VMs provisioned.” It is defined by measurable improvements in business operations, cost reduction, or speed to market.
Success criteria and baseline metrics from the old system must be established before the project begins. Without them, there is no way to prove ROI to stakeholders who only see the project’s cost.
Stop Reporting on Uptime and Start Reporting on Revenue
A common mistake is tracking only IT-centric KPIs. Server uptime and CPU utilization are important for technical teams but are meaningless to a CFO. A successful project translates technical achievements into business outcomes, shifting the IT department’s perception from a cost center to a value driver.
For example, instead of announcing a “migration to microservices,” report that you have “reduced time-to-market for new features from 6 months to 3 weeks.” The technical change is the how; the business impact is the why.
The balanced scorecard is an effective tool for this. It mandates a holistic view by tracking metrics across four key domains: financial, operational, performance, and security. This framework prevents declaring victory based on a single metric (e.g., performance) while ignoring a regression in another (e.g., security).
This provides a defensible, multifaceted narrative of the project’s value.
The Modernization Balanced Scorecard
To build your scorecard, select 2-3 specific, measurable KPIs for each category. Establish baseline metrics before starting and set a realistic target for 12-18 months post-launch.
This template provides a practical starting point.
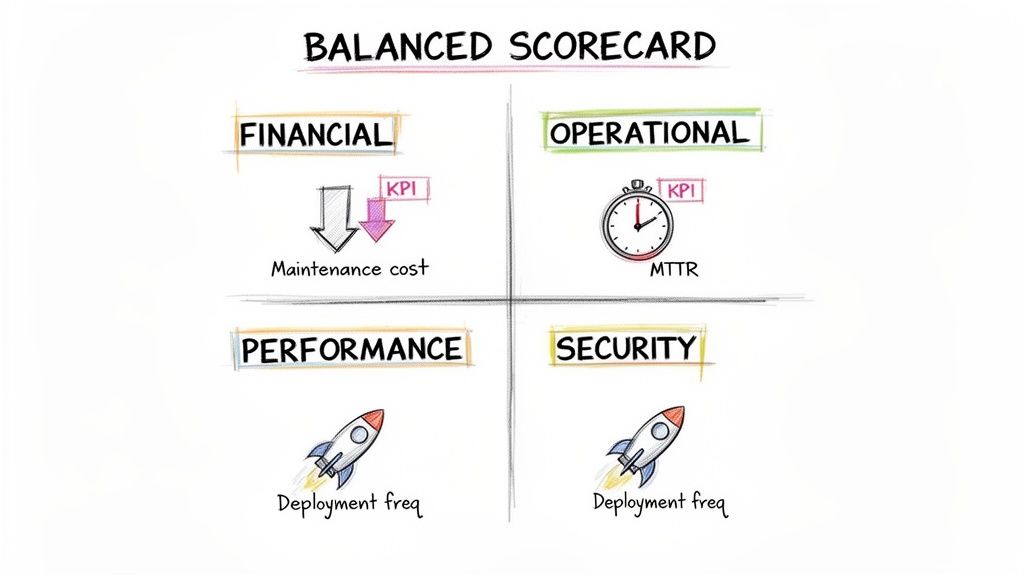
| Metric Category | Key Performance Indicator (KPI) | Baseline (Before) | Target (After) | Business Impact |
|---|---|---|---|---|
| Financial | System Maintenance Costs | $1.2M / year | < $400K / year | Reduces OpEx by 67%, freeing up budget for new projects. |
| Operational | Deployment Frequency | Quarterly | Bi-weekly | Boosts business agility, enabling faster response to market changes. |
| Performance | Mean Time to Recovery (MTTR) | 4.5 hours | < 15 minutes | Minimizes revenue loss and customer disruption during outages. |
| Security | Time to Patch Critical Vulnerabilities | 90+ days | < 7 days | Dramatically reduces the window of exposure to known security threats. |
These are not just tracking metrics; they are the foundation of the business case.
A planned 50-70% reduction in maintenance costs provides a concrete ROI calculation for the finance department. An increase in deployment frequency from quarterly to bi-weekly demonstrates a direct link between the project and competitive agility.
By defining success in these terms from the outset, you reframe the entire legacy system modernization initiative. It ceases to be a technical expense and becomes what it is: a strategic investment in the organization’s future. This is how you generate the unambiguous data required to prove the project’s strategic value.
Common Questions (And Unfiltered Answers) About Modernization
Every modernization project encounters practical questions that challenge high-level strategy. Here are direct answers to common concerns.
Is Modernization Always the Right Answer?
No. A common mistake is modernizing for the sake of adopting new technology. This is a resume-driven decision, not a business one.
Defer modernization if your legacy system is stable, meets business and compliance needs, and has predictable, low maintenance costs.
Another red flag is migrating from a common technology like COBOL to a niche modern language without a clear talent acquisition and training strategy. You are trading one form of technical debt for another.
If the business process supported by the system is scheduled for decommissioning within 2-3 years, do not attempt a full modernization. The ROI will not be achieved. Encapsulation or continued maintenance are the only financially sound options.
How Do We Deal With Decades of Historical Data?
With extreme caution. A failed data migration can compromise the entire project and corrupt critical business information. Do not attempt to move all data in a single cutover event.
The process must be phased, validated, and meticulously executed.
It begins with a comprehensive data audit to understand formats, quality issues, and data lineage. From there:
- Utilize ETL Tools: Use Extract, Transform, Load tools to cleanse, map, and reformat legacy data into the new schema within an isolated staging environment.
- Conduct Repetitive Test Migrations: Run the migration process repeatedly. Compare datasets, identify discrepancies, fix the mappings, and rerun. For financial data, automated reconciliation checks are non-negotiable to ensure decimal-level precision.
- Run Systems in Parallel: For a defined period, operate the old and new systems simultaneously, feeding both with live production data. This “dark launch” is resource-intensive but serves as the ultimate validation of data consistency before decommissioning the legacy system.
Attempting a “big bang” data migration without this level of rigor is a direct path to project failure.
What Exactly Is the Strangler Fig Pattern?
It is a risk-mitigation strategy for rewriting large monolithic applications. Instead of a single, high-risk replacement project, you incrementally replace pieces of the legacy system with new, modern services.
A proxy layer is placed in front of the legacy application to intercept all incoming requests.
Initially, the proxy routes all traffic to the legacy monolith. Then, a new microservice is built to replace a single piece of functionality (e.g., customer lookup). The proxy is configured to route all requests for that specific function to the new service, while all other traffic continues to the monolith.
This process is repeated, function by function. Over time, the new services “strangle” the legacy system until all its functionality has been migrated. Once the final component is replaced, the monolith can be decommissioned.
This approach is ideal for large, complex systems where a full rewrite presents unacceptable risk or cost. It keeps the project scope manageable, delivers continuous business value, and significantly reduces the probability of catastrophic failure.
Making the right call on a modernization partner is the single most important decision in this process. Modernization Intel provides the unbiased, data-driven intelligence you need—from real cost benchmarks to vendor failure modes—to choose a partner with confidence. Get Your Vendor Shortlist at https://softwaremodernizationservices.com.