What Is Vendor Due Diligence? A Risk-Tiered Survival Guide

Vendor due diligence is the systematic evaluation of third-party providers before and during partnerships: Organizations assess potential vendors’ financial stability, operational reliability, cybersecurity posture, compliance adherence, and overall risk profile to prevent downstream issues like data breaches, regulatory fines, or service disruptions—over 60% of breaches now stem from third parties, making this non-negotiable for enterprise resilience.
This isn’t a bureaucratic checkbox. It’s a critical survival tactic in an environment where your vendor’s security failure becomes your catastrophic data breach.
Unpacking The Modern Vendor Due Diligence Mandate

At its core, vendor due diligence answers one question: is this partner safe to integrate into our ecosystem? To get that answer, you must systematically evaluate their financial stability, operational reliability, cybersecurity posture, and compliance adherence. The goal is to prevent downstream issues like data breaches, regulatory fines, or service disruptions.
This level of scrutiny is no longer optional. According to a vendor risk management market analysis from Grandview Research, the market for vendor risk management tools, valued at USD 10.6 billion, is projected to exceed USD 25 billion by 2030. This growth is a direct response to a massive increase in vulnerabilities exploited in supply chain attacks.
Effective diligence isn’t about slowing down procurement. It’s about enabling the business to move faster and with more confidence by identifying the vendor risks that could derail critical projects like a cloud migration.
Buyer-Led vs. Seller-Initiated Diligence
The term “vendor due diligence” applies to two distinct contexts. In tech procurement, it’s buyer-driven to vet SaaS/cloud vendors, focusing on data handling and integration risks rather than pure financials. In M&A or divestitures, sellers commission independent vendor due diligence reports to proactively highlight strengths, mitigate perceived risks, and accelerate auctions.
| Assessment Area | Buyer-Led (Tech Procurement) | Seller-Initiated (M&A/Divestiture) |
|---|---|---|
| Primary Goal | Mitigate operational and security risks before signing a contract. | Accelerate a sale by proactively identifying and fixing issues buyers would find. |
| Who Leads It | The buyer’s technology, security, and legal teams. | The seller, who hires an independent firm to create a report for potential buyers. |
| Key Focus Areas | Cybersecurity posture, data privacy (GDPR/CCPA), scalability/reliability (SLAs), and integration complexity. | Financial health, intellectual property ownership, customer contracts, market position. |
| Outcome | A go/no-go decision on the partnership, or a list of required security remediation. | A formal VDD report shared with bidders to build confidence and speed up the deal. |
While both are important, the buyer-led process is what protects your organization from integrating a critical vulnerability into your tech stack.
“A vendor assessment that only looks at financials is like a physical that only checks blood pressure. It misses the underlying conditions—like a weak security posture or poor data governance—that are far more likely to cause a critical failure in a technology partnership.”
The Strategic Imperative
Organizations that treat due diligence as a compliance task miss the strategic value. A robust process ensures each new vendor strengthens, rather than weakens, operational resilience.
It forces the conversations that move beyond a sales pitch into verifiable proof. For instance, a vendor might claim 99.99% uptime. A diligence check might uncover a disaster recovery plan with a 24-hour recovery point objective (RPO), meaning a potential loss of an entire day’s data.
Diligence finds this mismatch before it becomes an incident. This mindset shift—from gatekeeping to strategic enablement—is what separates organizations that innovate safely from those constantly reacting to supplier-induced failures.
The Four Pillars Of A Modern Diligence Framework
A modern vendor assessment is a forensic examination, not a simple credit check. Core assessment pillars go beyond financials to tech-specific risks: evaluate cybersecurity (breach history, encryption, incident response), data privacy (GDPR/CCPA compliance, subprocessors), scalability/reliability (SLAs, disaster recovery), and operational maturity (vendor’s own fourth-party diligence)—poor scores here have derailed more cloud migrations than cost overruns.
Pillar 1: Cybersecurity Posture
When you onboard a vendor, you inherit their security weaknesses. Assessing their cybersecurity posture is non-negotiable, particularly if they handle sensitive data. Cybersecurity and data protection dominate tech vendor risks: probe for zero-trust architectures, employee training, subcontractor oversight, and breach notification timelines—vendors handling PII or powering core systems must demonstrate maturity equivalent to your internal standards, or negotiate contractual remedies like indemnification.
Key artifacts to demand include:
- SOC 2 Type II Report: This is the standard. It’s an independent audit report detailing how a company protects customer data and, more importantly, how well those controls function over time.
- Recent Penetration Test Results: Request the executive summary from their latest third-party penetration test. This demonstrates proactive testing against real-world attack methods.
- Incident Response Plan: Review their plan for handling a security breach. Does it clearly outline how and when they will notify you? A vague plan indicates a lack of preparedness.
Pillar 2: Data Privacy And Compliance
Compliance reflects a vendor’s operational discipline. A vendor that is casual with data privacy regulations like GDPR or CCPA is a liability, exposing your organization to potential fines and reputational damage.
A vendor’s attitude toward data privacy indicates their respect for your data. If they’re lax with compliance, they are likely lax with security and reliability.
Essential compliance checks include:
- GDPR/CCPA Adherence: Verify their policies for data subject rights and lawful processing. Review their Data Processing Addendum (DPA) early in the process.
- Subprocessor Management: Demand a full list of their third-party vendors (subprocessors) that will have access to your data. Ask how they conduct diligence on those fourth parties.
- Industry-Specific Certifications: For regulated industries like healthcare or finance, confirm they hold required certifications like HIPAA or PCI DSS.
Pillar 3: Operational Reliability
A flashy UI is irrelevant if the service is unreliable. Operational reliability determines if the vendor will be a dependable partner or a source of constant disruption.
Core reliability indicators to check are:
- Service Level Agreements (SLAs): Look beyond the uptime percentage (99.9% vs. 99.99%). The critical details are in the penalties for a breach. Meaningful financial credits for downtime show they have skin in the game.
- Disaster Recovery (DR) Plan: Ask for their Recovery Time Objective (RTO) and Recovery Point Objective (RPO). These two metrics define how quickly they can restore service and how much data might be lost in a worst-case scenario.
- Fourth-Party Risk Management: How does the vendor manage risks from their own critical suppliers, like their cloud provider? A major outage at a public cloud provider can cause a domino effect; a mature vendor will have a contingency plan.
Pillar 4: Financial Viability
Will this vendor be in business to deliver on long-term commitments? Financial and reputational checks reveal hidden viability threats. This is critical for startups or private companies where financials are not public. Assess stability (credit reports, funding rounds for startups), litigation history, and ESG factors—SaaS vendors with runway under 18 months or recent layoffs signal potential service degradation, impacting your modernization roadmaps.
Key financial health checks include:
- Funding Status and Runway: For startups, understand their funding history and cash runway. A vendor with less than 18 months of cash on hand is a high-risk dependency.
- Litigation History: A history of lawsuits from customers or former employees can indicate underlying operational or ethical problems.
- Customer Concentration: If a large percentage of their revenue (over 25%) comes from a single customer, their stability is tied to that one relationship.
How To Implement A Risk-Tiered Diligence Process
Applying the same level of intense scrutiny to every vendor is inefficient. Adopt a risk-tiered approach to allocate resources efficiently: classify vendors by criticality (e.g., access to sensitive data, business impact)—high-risk (e.g., cloud data platforms) demand deep dives into SOC 2 reports and penetration tests; low-risk get lightweight questionnaires—preventing over-engineering while catching 90% of material risks early.
This approach focuses forensic-level analysis where it matters most.
Classifying Vendors Into Risk Tiers
The classification system should be based on two factors: data access and business criticality. If a vendor handles sensitive data or their failure would cause a significant business disruption, they are classified as high-risk.
- High-Risk Tier: Critical partners with access to sensitive data (PII, PHI, financial records) or whose failure would be catastrophic. Examples include cloud infrastructure providers, core payment processors, or data migration partners.
- Medium-Risk Tier: Vendors supporting important but non-essential functions. They might handle less sensitive business data. Examples include marketing automation platforms, CRM systems, or project management tools.
- Low-Risk Tier: Suppliers with no access to sensitive data, and whose failure would be a minor inconvenience. This tier includes vendors for office supplies, facilities management, or corporate travel.
Tailoring Diligence Activities To Each Tier
Once a vendor is classified, the required diligence activities should be clearly defined. This creates a consistent and defensible process by matching the level of effort to the level of risk.
A risk-tiered framework isn’t about doing less due diligence; it’s about doing the right diligence. It channels your team’s expertise toward the third-party relationships that could cause catastrophic failure.
The following table shows how this works in practice.
| Risk Tier | Example Vendor Type | Required Diligence Activities |
|---|---|---|
| High | Cloud Infrastructure Provider (AWS, GCP), Core Payment Processor | Full Security Architecture Review, SOC 2 Type II Analysis, Penetration Test Results, Incident Response Plan Review, Direct Interviews with Security Team |
| Medium | Marketing Automation Platform, Project Management Tool | Standardized Security Questionnaire (e.g., CAIQ), Proof of Key Certifications (ISO 27001), Data Processing Agreement (DPA) Review |
| Low | Office Supply Vendor, Corporate Catering Service | Basic Financial Health Check, Sanctions & Watchlist Screening, Acceptance of Standard Terms |
This segmentation ensures that your most experienced security personnel are not occupied with low-risk vendors.
This decision tree shows how a modern vendor assessment focuses on four key pillars which are the basis for a risk-tiered diligence process.
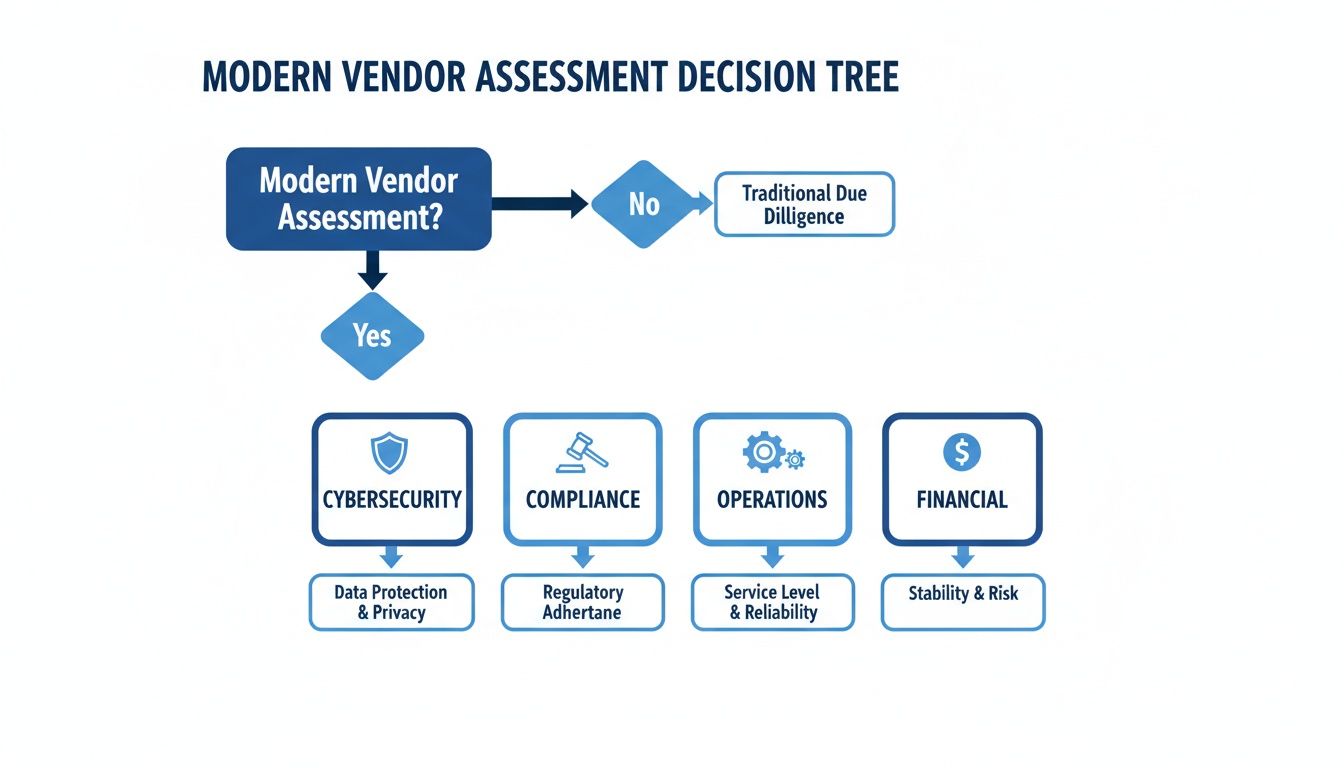
As the chart illustrates, these four pillars—Cybersecurity, Compliance, Operations, and Financials—form the foundation of any robust diligence framework.
High-risk vendors require a deep dive into each pillar. For a detailed guide, our technical due diligence checklist provides a playbook for these high-stakes assessments.
Medium-risk vendors may only need to complete a standardized security questionnaire, like a Consensus Assessments Initiative Questionnaire (CAIQ), and provide proof of certifications. Low-risk vendors often require only an automated check of their financial standing and public records.
This pragmatic approach is key to building a scalable and effective vendor due diligence program. Leverage automation and standardized tools to scale without chaos: manual spreadsheets fail at enterprise volume; use platforms for questionnaires, evidence collection, risk scoring, and workflow automation—reducing onboarding time by 50-70% while ensuring audit-ready trails for regulators or board inquiries.
Why Ongoing Vendor Monitoring Is Non-Negotiable
Initial diligence occurs pre-contract; ongoing monitoring is mandatory. An upfront assessment is a snapshot in time. A vendor’s risk profile is dynamic, changing with market pressures, personnel changes, and their own supply chain. Treating diligence as a one-time event is a significant risk, particularly with the rise of sophisticated supply chain attacks. Perform thorough upfront checks during RFP/shortlisting to inform negotiations; post-onboarding, schedule reviews based on tier (annual for high-risk) plus continuous signals monitoring (e.g., security ratings, news alerts)—static one-time checks expose organizations to evolving threats.
The Static Diligence Trap
Relying solely on an initial check creates a critical blind spot. A Gartner survey found that 83% of firms identify vendor-related issues only after the partnership begins.
This statistic highlights the limitations of static, point-in-time checks. By the time a problem is discovered, such as a critical vulnerability, the damage may already be done. Ongoing monitoring moves an organization from reactive cleanup to proactive risk management. For more on this, check out the vendor risk management market report from Mordor Intelligence.
The point of ongoing monitoring isn’t to catch vendors making mistakes. It’s to spot risk drift—the slow degradation of a vendor’s security or operational posture—before it becomes a crisis.
A Framework for Continuous Monitoring
Effective monitoring is about establishing a practical, risk-tiered framework that combines scheduled check-ins with automated, continuous signals.
A solid approach includes these three components:
- Scheduled Periodic Reviews: Formal, in-depth checkups scheduled based on the vendor’s risk tier. High-risk vendors should undergo a thorough annual review of their SOC 2 report, penetration test results, and incident response plans.
- Automated Security Ratings: Use tools that continuously scan a vendor’s external attack surface for new vulnerabilities or misconfigurations. These platforms provide an objective security score and alert you to sudden changes.
- Public Red Flag Tracking: Monitor public signals that could indicate rising risk, such as news of a data breach, executive turnover, layoffs, or negative financial reports.
Integrating Monitoring into the Vendor Lifecycle
Monitoring must be integrated into vendor lifecycle governance. It should be a formal, required stage for all active vendors, especially those in high- and medium-risk tiers. Cross-functional involvement ensures holistic decisions: involve procurement, legal, security, finance, and engineering leaders early—siloed reviews miss integration risks (e.g., API compatibility in data stacks) or contractual traps, leading to expensive rework post-go-live.
The process needs to be clear:
- Define Triggers: What events automatically initiate a reassessment? Examples include a security rating dropping below a threshold or a change in vendor ownership.
- Assign Ownership: Who is responsible for acting on these triggers? This typically falls to the vendor relationship owner, in collaboration with security and procurement.
- Document Outcomes: All monitoring activities and their results must be documented in a central system to create an audit trail.
By treating vendor relationships as partnerships that require ongoing attention, you transform due diligence from a static gate into a continuous process.
Common Red Flags And How To Spot Them Early
Identifying a high-risk vendor requires professional skepticism. Your job is to look past the sales presentation for the red flags that demand deeper investigation.
Uncovering a deal-breaker before signing a contract is a success, not a wasted effort.
Financial Instability Signals
A vendor’s financial health is a predictor of their long-term reliability. A company facing financial pressure is more likely to cut corners on security or support.
Look for these financial warning signs:
- Short Financial Runway: For a startup, a cash runway under 18 months is a major red flag, signaling financial pressure that could lead to service degradation.
- Recent Layoffs or High Turnover: Sudden staff reductions or the departure of key executives can indicate internal turmoil and instability.
- Unresolved Litigation: A history of lawsuits from customers or regulators can reveal operational problems not mentioned in marketing materials.
Operational And Security Evasiveness
When a vendor is vague or defensive about their security and operational practices, it often means they have something to hide. Transparency is a mark of a mature provider.
A vendor’s refusal to share a recent SOC 2 report should be treated as a critical failure of the due diligence process. It’s the modern equivalent of a restaurant owner refusing to let a health inspector into the kitchen.
Watch for these behaviors:
- Withholding a SOC 2 Report: Reluctance to share their latest SOC 2 Type II report is a dealbreaker. It suggests they either don’t have one or its findings are unfavorable.
- Vague Answers on Subprocessors: If they cannot provide a clear list of their own third-party vendors (subprocessors) that will handle your data, they lack basic data governance.
- No Clear Incident Response Plan: A hesitant answer when asked about their breach notification process indicates they are not prepared for a security incident.
Cybersecurity Weaknesses in Plain Sight
A vendor’s weak security posture is a direct threat to your business. The Verizon Data Breach Investigations Report found that 15% of data breaches originated from third-party suppliers, following a significant spike in exploited vulnerabilities. You can learn more about the growing importance of enhanced due diligence on polarismarketresearch.com.
Many organizations struggle to maintain a robust security program. If a potential vendor shows signs of an immature security culture, it’s worth understanding how top-tier DevOps consulting companies embed security into their development lifecycle. This provides a benchmark for what to expect from any partner. These red flags should trigger immediate follow-up questions that demand concrete proof of remediation.
Future-Proofing Your Vendor Governance Strategy
Vendor due diligence has evolved from a defensive procurement exercise into a source of strategic advantage. Future-proof by embedding diligence into vendor lifecycle governance: as AI/ML vendors proliferate and regulations tighten (e.g., DORA in EU), build frameworks that adapt to emerging risks like model bias or deepfake vulnerabilities—strong processes turn vendor selection from a gate to a strategic advantage, enabling faster innovation with controlled exposure through 2030.
Adapting to Emerging Technology and Regulatory Risks
The vendor landscape is becoming more complex with the proliferation of AI and machine learning vendors. Traditional diligence processes may not be equipped to evaluate risks like model bias or data poisoning.
Simultaneously, regulations are tightening. Mandates like the Digital Operational Resilience Act (DORA) in the EU require firms to demonstrate resilience across their entire digital supply chain.
An adaptable framework must incorporate these new risk vectors. It needs to evolve to ask the right questions, whether that’s investigating an AI vendor’s training data or confirming a cloud provider’s regional compliance. For a deeper look at managing these types of technology risks, check out our guide on executing a comprehensive cloud migration risk assessment.
Championing Cross-Functional Governance
Siloed reviews are a common point of failure. When procurement, legal, security, and engineering conduct separate checks, critical integration risks are often missed.
A mature vendor governance program doesn’t just block bad vendors; it enables the business to partner with innovative new ones faster and more safely. It turns risk management from a cost center into a competitive edge.
The solution is to embed diligence into the entire vendor lifecycle, driven by a cross-functional team. This creates a holistic view where security’s concerns are weighed alongside finance’s analysis and engineering’s assessment of technical fit.
This collaborative approach prevents expensive, downstream failures that result from incomplete assessments and builds a resilient vendor ecosystem that supports your modernization roadmap.
Got Questions? We’ve Got Answers.
Here are direct answers to common questions about vendor due diligence.
Vendor Due Diligence vs. Vendor Risk Management — What’s the Difference?
Vendor Due Diligence is the intensive investigation conducted before a contract is signed. It is a project with a defined start and end.
Vendor Risk Management (VRM) is the comprehensive, ongoing program that includes initial diligence, continuous monitoring, performance tracking, and offboarding. Diligence is the critical first step in the long-term VRM process.
How Can a Small Company Do This Without a Big Budget?
Focus resources on high-risk vendors—those handling sensitive data or core business functions. For these partners, obtaining and reviewing their latest SOC 2 report is essential.
For lower-risk vendors, use lightweight security questionnaires and conduct basic online checks for public data breaches or financial red flags. The goal is to apply the right level of scrutiny to the right partners.
A SOC 2 report isn’t just another piece of paper. It’s an independent, third-party audit that verifies a vendor’s claims about their security, availability, and confidentiality controls. It’s what turns their marketing promises from “trust us” into “here’s the proof.”
What’s the Single Biggest Red Flag to Watch For?
Evasiveness.
If a vendor is reluctant to share a recent SOC 2 report, cannot provide a clear answer about their subprocessors, or fails to detail their incident response plan, it is a major red flag.
Mature, secure partners are transparent about their controls. A lack of transparency often indicates a significant operational or security weakness.
Making defensible vendor decisions requires unvarnished truth, not marketing fluff. Modernization Intel delivers data-driven intelligence on implementation partners, including real costs, documented failure rates, and validated specializations. Get the unvarnished truth at https://softwaremodernizationservices.com.
Need help with your modernization project?
Get matched with vetted specialists who can help you modernize your APIs, migrate to Kubernetes, or transform legacy systems.
Browse Services