A Practical Guide to Enterprise Mobile Applications

Enterprise mobile applications aren’t consumer downloads. They are specific tools designed to solve a business problem, integrating directly into core systems like ERP and CRM under stringent security protocols. Success isn’t measured in app store reviews or download volume; it’s measured in operational impact. Did the application reduce inventory shrinkage by 3%? Did it shorten the sales cycle from 120 days to 95? That is the only scoreboard that matters.
Defining the Business Case for Enterprise Mobility
An enterprise mobile application is a secure, managed connection from an employee’s device into core business systems. It is engineered to enable a specific user to perform a specific function, regardless of location.
The primary challenge and source of value is deep system integration. These are not standalone utilities. To provide a positive ROI, they must reliably read from and write back to systems of record, whether that’s SAP, Oracle, or Salesforce. This direct connection is what distinguishes an enterprise tool from a consumer-grade application.
Core Functions and Business Impact
These applications are built to drive measurable results. While a refined UI is beneficial, if a logistics application doesn’t reduce shipping delays by a quantifiable margin, it has failed. The objective is to translate mobile access into specific business value.
Here are common implementations:
- Field Service Management: Provides technicians with mobile access to job schedules, parts inventory, and customer history. Success is measured by a reduction in return visits (“truck rolls”) or an increase in first-time fix rates.
- Sales Enablement: Equips sales teams with mobile access to CRM data, product catalogs, and quoting tools. Success is measured in shorter sales cycles and improved CRM data accuracy.
- Logistics and Supply Chain: Applications for warehouse inventory scanning, real-time fleet tracking, or digital proof-of-delivery. Value is directly tied to inventory accuracy and on-time delivery KPIs.
- Internal Communications and HR: Secure channels for corporate announcements, workflow approvals, or employee self-service tasks like PTO requests. The goal is to drive adoption and reduce friction in internal processes.
Security Is a Foundational Requirement
The data flowing through these applications includes sensitive customer information, financial records, and proprietary operational plans. This makes security a non-negotiable architectural foundation. A significant number of mobile applications fail basic security assessments, creating substantial risk.
According to research firm Gartner, most mobile breaches will not result from sophisticated attacks on the device. They will occur due to application-level misconfigurations. This places the responsibility on secure application design from the outset.
This means components like end-to-end data encryption, secure on-device data storage, and integration with Mobile Device Management (MDM) platforms are baseline requirements, not optional features. An application that leaks corporate data, regardless of its functionality, is a net liability. The objective is to create a tool that is both functionally effective and fundamentally secure.
Choosing the Right Architectural Blueprint
Selecting an architecture for an enterprise mobile application is a strategic decision that determines long-term costs, performance capabilities, and maintenance overhead. The frontend framework often receives the most attention, but the make-or-break complexity resides in the backend integration connecting the app to core business systems.
Incorrect architectural choices can result in an expensive tool with low user adoption.
For example, a sales quoting tool that exhibits a 10-second lag while querying an on-premise ERP is operationally ineffective, regardless of its UI design. The architecture must serve the business requirement, not just adhere to a development trend.
The Three Core Architectural Models
Most enterprise mobile applications use one of three architectural models. Each presents a different set of trade-offs between performance, development velocity, and user reach. No single option is “best”; the correct choice depends on the application’s functional requirements and user base.
-
Native Apps: These are built for a specific operating system (iOS or Android) using platform-specific languages (Swift for iOS, Kotlin for Android). This approach delivers the highest possible performance, direct access to device hardware (e.g., GPS, camera), and the most fluid user experience. The primary trade-off is cost, as it requires building and maintaining two separate codebases.
-
Hybrid Apps: This approach uses standard web technologies (HTML, CSS, JavaScript) for the core application, which is then enclosed in a native wrapper. This allows for distribution through app stores. The “write once, run anywhere” strategy can reduce initial development costs by 30-40% compared to a dual-native approach. The trade-off is potentially reduced performance and reliance on plugins for accessing device-specific features. For a detailed analysis, see our guide on hybrid application development in our detailed guide.
-
Progressive Web Apps (PWAs): A PWA is an enhanced website that runs in a browser but can be installed on a user’s home screen, send push notifications, and offer limited offline functionality. PWAs provide the broadest reach with the simplest deployment model, bypassing app store approval processes. However, they have the most restricted access to device hardware and may lack the performance required for data-intensive enterprise tasks.
Enterprise App Architecture Trade-Offs
The architectural decision involves balancing several key variables. This table outlines how Native, Hybrid, and PWA models compare against critical enterprise criteria.
| Architecture | Performance & UX | Backend Integration | Development Cost & Speed | Best-Fit Scenario |
|---|---|---|---|---|
| Native | Highest possible performance and seamless UX. Full hardware access. | Direct, low-latency API calls. Secure and reliable. | Highest cost, slowest speed. Requires two separate codebases. | High-performance tools for field technicians, data-intensive sales applications. |
| Hybrid | Good performance, but can feel less fluid than native. Hardware access via plugins. | Standard API integration, but plugins can add complexity. | Moderate cost, faster speed. “Write once, run anywhere” efficiency. | Internal employee apps, B2B portals, content delivery platforms. |
| PWA | Performance is browser-dependent. Most limited hardware access. | Standard API integration. Offline capability is limited. | Lowest cost, fastest speed. Deploys like a website. | Simple data entry forms, event applications, internal directories. |
The optimal choice is context-dependent. The architecture for a field service application is likely unsuitable for a company-wide directory.
Critical Backend Components
The frontend model is only one part of the architecture. The backend is where most enterprise application projects succeed or fail. This is the infrastructure that connects the mobile interface to existing systems, from modern cloud services to legacy mainframes.
The success of an enterprise mobile app is less dependent on its UI polish and more on the resilience of its backend integrations. If the data is not reliable, real-time, and secure, the app is merely a well-designed facade.
These are non-negotiable backend components:
- API Gateway: This functions as the single, secure entry point for all mobile traffic into the corporate network. It manages user authentication, enforces rate limiting, and routes traffic, thereby isolating internal systems from direct internet exposure. A properly configured gateway is a primary security control.
- Middleware: Many organizations rely on legacy systems that do not use modern APIs. Middleware acts as a translator, converting the application’s modern API calls into protocols that older mainframes or on-premise databases can process. This layer is often the most complex and fragile part of the integration.
- Mobile Device Management (MDM): MDM integration allows the organization to control the application and its data on the device. It provides IT with the capability to remotely wipe corporate data from a lost device, enforce passcode policies, and prevent data exfiltration. For any application handling corporate data, particularly on employee-owned devices, MDM is essential.
Navigating the Security and Compliance Minefield
For enterprise mobile applications, security is not a feature; it is the foundation. A data breach originating from an insecure field service app can result in regulatory fines, brand damage, and exposure of proprietary data.
The risk is typically not a sophisticated, targeted attack but a predictable result of mismanaged priorities. Most security failures stem from basic misconfigurations and overlooked fundamentals.
Research from Gartner has consistently shown that the majority of mobile security breaches are due to application-level flaws, not vulnerabilities in the mobile operating system. This places the burden of security on the development and deployment strategy.
The initial architectural choice has significant security implications.
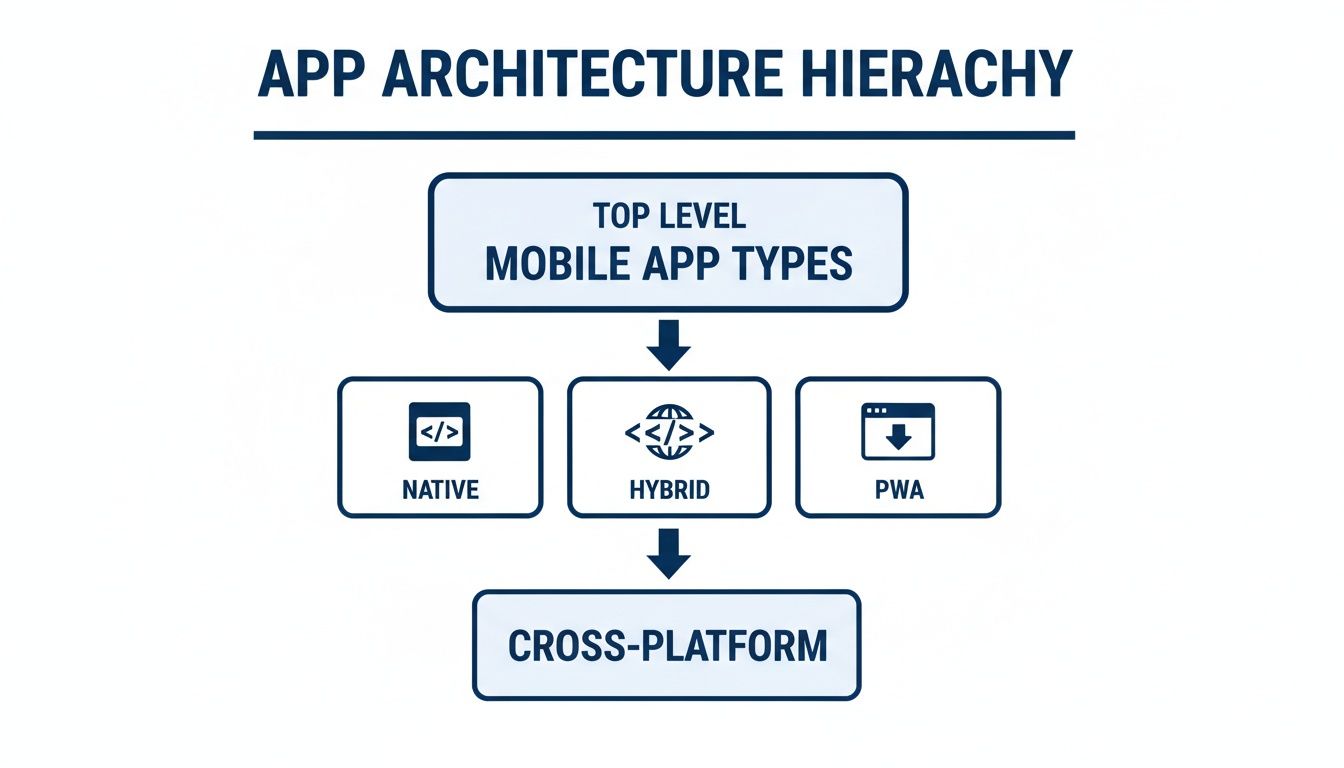
As the diagram illustrates, a Native application provides maximum control but also doubles the maintenance burden by creating two separate attack surfaces (iOS and Android). A PWA, conversely, operates within a sandboxed browser, introducing a different set of web-based vulnerabilities that require mitigation.
Translating Compliance into Code
Regulations like GDPR, HIPAA, and SOC 2 are not just legal frameworks; they are technical specifications for data handling. A common cause of non-compliance is the failure to translate these requirements into concrete architectural decisions. An application can be functionally perfect yet represent a significant liability if it violates data sovereignty laws.
Here’s how regulatory rules translate into engineering tasks:
- End-to-End Data Encryption: Data must be encrypted in transit using protocols like TLS 1.3 and at rest on the device. Insecure on-device data storage remains a common and critical vulnerability.
- Secure API Design: The application’s security is contingent on the security of its APIs. An API that exposes excessive data or has weak authentication can create a backdoor into corporate systems.
- Immutable Audit Logs: It is necessary to prove who performed what action and when. This requires creating detailed, tamper-proof logs for every critical event—from user login to record modification—and transmitting them to a secure, centralized logging system.
- Multi-Factor Authentication (MFA) and SSO: Relying on single-factor password authentication for an application accessing sensitive data is insufficient. Integration with an enterprise identity provider for Single Sign-On (SSO) and enforcement of MFA are baseline requirements.
The most significant risk in enterprise mobility is not an attacker targeting a single device. It is an insecure application architecture that exposes sensitive data across thousands of devices by default. The problem is systemic.
Common and Costly Security Failures
Pressure to release features often leads to security being treated as a final-stage gate rather than a continuous process. This approach is predictably expensive.
These are frequent and avoidable failure modes:
- Man-in-the-Middle (MitM) Attacks: An employee connects to public Wi-Fi. If the application does not implement certificate pinning, an attacker on the same network can intercept traffic, capturing credentials and session tokens.
- Insecure Data Storage on BYOD Devices: On personal devices (Bring Your Own Device), the boundary between corporate and personal data is blurred. An application that caches sensitive data in an unencrypted local file creates a high risk of data leakage if the device is lost, stolen, or compromised by malware.
- Unintended Data Leakage: This occurs when an application inadvertently exposes sensitive data to other applications on the device via a shared clipboard, insecure file storage, or screen captures. Strict data containment is necessary.
A practical approach is to assume a breach is possible and design for resilience. A Zero Trust Architecture design is an effective model for mobile security, as it requires strict verification for every access request, which significantly reduces the potential impact of a compromised device or stolen credential.
Calculating the True Cost of Enterprise Mobility
The initial development quote for an enterprise mobile app is only a fraction of the total cost of ownership (TCO). The majority of costs are operational expenses that are frequently underestimated. Focusing solely on the upfront build cost is a common mistake that leads to underfunded projects that fail due to a lack of ongoing maintenance.
The market for enterprise mobile applications is projected to grow from USD 136.84 billion to USD 385.56 billion by 2031, according to this mobile enterprise application research. As investment increases, accurate budgeting becomes critical for project viability.
A realistic budget must account for all costs required to keep the application secure, functional, and relevant over its lifecycle.
Deconstructing the Hidden Costs
The initial development contract or first-year salaries are just the starting point. Significant costs are incurred over the application’s 3-5 year lifespan.
- Ongoing API and Backend Maintenance: The APIs connecting the app to backend systems (ERP, CRM) are subject to changes. When a backend system is updated, APIs can break. Remediation requires developer time, typically consuming 15-20% of the initial development cost annually.
- Mandatory OS Platform Updates: Apple and Google release major OS updates annually. These updates often deprecate old frameworks and introduce new security requirements that can cause application failure. Allocating developer time for compatibility is mandatory.
- Backend Server and Cloud Infrastructure: The application runs on the device, but the data is processed and stored on servers. These servers incur monthly costs for hosting, compute, and storage. These operational costs, if ignored, can lead to poor application performance. Our guide on effective cloud cost optimization strategies provides more detail.
- Security Audits and Penetration Testing: For applications that handle sensitive data, annual security audits are a compliance requirement. A professional penetration test can cost between $5,000 and $20,000 per audit.
Range-Bound Cost Data for Common Projects
Qualitative terms like “expensive” are not useful for financial planning. The cost of an enterprise application is primarily a function of its integration complexity.
Here are some real-world, range-bound estimates.
The single largest cost driver for an enterprise mobile application is rarely the user interface. It is almost always the complexity of integrating with, and synchronizing data between, multiple legacy backend systems.
Project Cost Examples
| Application Type | Primary Function | Key Feature | Estimated Cost Range |
|---|---|---|---|
| Field Service App | Task management for technicians | Offline data synchronization, ERP integration | $150,000 - $300,000+ |
| Sales Enablement Tool | Mobile CRM and quoting | Real-time data sync with Salesforce/Dynamics | $100,000 - $225,000 |
| Internal Comms App | Secure messaging, directory | SSO integration, push notifications | $50,000 - $90,000 |
| Logistics & Tracking App | Inventory and fleet management | Barcode scanning, GPS integration | $120,000 - $250,000 |
These figures represent the initial build cost. A sound financial model should allocate an additional 15-25% of the initial cost for each year of the application’s lifecycle to cover ongoing maintenance.
Build Custom vs Buy a Platform
A key strategic decision is whether to build a custom enterprise mobile application or license a Mobile Enterprise Application Development Platform (MEADP). This choice impacts budget, timeline, and long-term flexibility.
There is no single correct answer, only the appropriate choice for a specific context.
The global Mobile Enterprise Application market is valued at USD 28.43 billion and is projected to reach USD 135.02 billion by 2032. A significant portion of this growth is driven by companies using platforms to accelerate development, a trend analyzed in market research. You can gain more context by reading the full research about the expanding enterprise application market.
An incorrect decision can result in a multi-year commitment to an unsuitable technology stack and an expensive tool with low user adoption.
When Custom Development is Non-Negotiable
Building a custom application is the most capital- and time-intensive option, but it is sometimes necessary. Platforms achieve speed through standardization. If your core business process is a competitive differentiator, standardization is counterproductive.
Consider a custom build when:
- Your workflow provides a competitive advantage. If the application must support a unique, proprietary process, forcing it into a standardized platform will diminish its value.
- Deep hardware integration is required. Direct communication with industrial scanners, medical devices, or custom IoT sensors often necessitates a custom native build for reliable control.
- Performance is a critical requirement. For applications requiring high-performance graphics, complex offline data processing, or real-time calculations, a native, custom-built application will outperform a platform-based solution.
The Case for Buying a Platform
MEADPs and low-code/no-code (LCNC) platforms have matured. They offer a trade-off: reduced control and uniqueness in exchange for significantly accelerated development and lower costs. For many standard internal business functions, this is an efficient approach.
A platform approach fundamentally changes the development equation. Instead of allocating 80% of your budget to foundational components like authentication and UI kits, you begin with these components already in place and focus primarily on implementing business logic.
Platforms are highly effective for digitizing standard, repeatable internal processes.
- Digitizing Standard Internal Processes: Examples include expense reporting, HR approvals, or simple inventory check-in forms. These are solved problems. Building custom applications for such functions is an inefficient use of resources.
- Reducing Time-to-Market: When a solution is needed quickly, a platform can deliver a working application in weeks rather than months or years. This allows for the rapid deployment of a Minimum Viable Product (MVP) to test a concept with users.
- Addressing Resource Constraints: For organizations without a dedicated mobile development team, platforms are often the only feasible option. They enable business analysts or IT generalists to develop applications.
The decision criteria can be simplified to a single question: does this application support a core competitive differentiator, or does it support a standard business function? If the former, build. If the latter, buy.
When to Kill an Enterprise App Project Before It Starts
Building a custom enterprise mobile application is often seen as a default step in modernization. However, the most strategic decision is sometimes to build nothing.
Before committing a six-figure budget, it is critical to determine if the proposed application is a genuine solution or an expensive remedy for a fundamentally broken business process.
The “App-as-a-Symptom-Fixer” Trap
A common error is misdiagnosing a flawed workflow as a technology gap. If an inventory management process is based on inconsistent spreadsheets and manual data entry, a mobile app will not create order; it will digitize the existing chaos. The result is a mobile, and more expensive, broken process.
Technology should solve a problem, not mask its symptoms. For example, if a sales team’s CRM data entry is inconsistent and incomplete, is the root cause a lack of mobile access, or is the CRM form itself an overly complex, 50-field document? Building an app in this scenario merely transfers the point of failure from a desktop interface to a smartphone screen.
A process audit should be conducted before greenlighting any project.
- Map the As-Is Workflow: Document every step, handoff, and decision point to identify the actual bottlenecks.
- Identify the Root Problem: Is the issue a lack of mobile data access, or is the source data itself inaccurate? Is the process redundant?
- Quantify the Inefficiency: Calculate the cost of the broken process in terms of wasted labor hours and the financial impact of errors. This figure becomes the baseline for evaluating any proposed solution.
The most expensive enterprise mobile apps are those built to automate a process that should have been eliminated. An app cannot fix a workflow that is illogical or inefficient at its core.
Look for Cheaper, Faster Alternatives First
Even with a sound business process, a custom-built app is not always the optimal solution. The “build an app” mindset can overlook more practical, lower-risk alternatives.
These alternatives can often deliver 80% of the value for a fraction of the cost and maintenance overhead of a custom application.
Consider these options first:
- Responsive Web Portals: For many internal tasks—viewing dashboards, submitting forms, or accessing a knowledge base—a modern, mobile-friendly web portal is sufficient. There is no app store approval process, it works on any device with a browser, and it eliminates the need to maintain separate codebases for iOS and Android.
- Existing Platform Integrations: If your organization already uses a major platform like Salesforce, ServiceNow, or an ERP system, investigate their existing mobile capabilities. It is almost always more cost-effective and faster to extend the functionality of a platform you already license than to build a competing solution from scratch. A simple integration may solve the entire problem.
The goal is not to avoid technology, but to apply it judiciously. Resisting the impulse to default to a custom application can be the most fiscally responsible and strategically sound decision.
Common Questions, Straight Answers
Here are direct answers to common questions from CTOs and engineering leaders.
What’s the Single Biggest Mistake Companies Make?
Focusing on the front-end UI while underestimating the backend integration.
The most common point of failure is a drastic underestimation of the complexity and ongoing cost of backend integration and maintenance. Many projects allocate significant resources to UI design but underfund the development of robust APIs, reliable data synchronization with systems like CRM or ERP, and a long-term plan for OS updates and security patches.
An application with a polished UI that cannot reliably transmit data is an expensive failure. This oversight is a primary driver of low user adoption and negative ROI.
How Long Does This Actually Take?
The timeline is dictated primarily by backend complexity. A simple, single-purpose internal application built on a low-code platform might be completed in 2-4 months.
However, this is not typical for an enterprise project.
- A moderately complex application connecting to one or two backend systems generally requires 4-9 months.
- A highly complex, custom application with multiple integrations, offline functionality, and stringent security requirements can take 9-18 months or longer from initial concept to launch.
This timeline is for version 1.0. The project then transitions to a permanent operational cost for ongoing maintenance.
The initial build is the first phase. A successful enterprise application requires a multi-year commitment to security patching, OS compatibility updates, and API maintenance. It is a product, not a project.
How Do You Actually Measure the ROI?
ROI is measured by operational impact, not vanity metrics like download counts. The business case must be built on quantifiable improvements to core business functions.
Track KPIs that are meaningful to financial stakeholders:
- Reduced operational costs: Quantify savings from reduced paperwork, fewer manual data entry errors, or lower travel expenses.
- Increased productivity: Measure hours saved per technician per week or the number of additional sales quotes processed per day.
- Improved data accuracy: Calculate the cost of remediating poor data in the ERP and demonstrate how the application reduces this cost.
- Shorter process cycles: Quantify the reduction in time required to resolve a sales quote, inventory check, or support ticket.
The ROI calculation is straightforward: compare the total cost of ownership (initial build + 2-3 years of maintenance) against the financial gains from these operational improvements over the same 2-3 year period.
Making the right technology and partner decisions is the difference between success and a multi-million dollar write-off. Modernization Intel gives you unbiased, data-driven intelligence on over 200 implementation partners. We help you see past the sales pitches to understand a vendor’s true specializations, realistic costs, and common failure points. Get your vendor shortlist.
Need help with your modernization project?
Get matched with vetted specialists who can help you modernize your APIs, migrate to Kubernetes, or transform legacy systems.
Browse Services