A Technical Leader's Guide to Budgeting for IT Modernization

Budgeting for IT modernization is a high-risk activity. Miscalculations don’t just lead to budget overruns; they are a primary driver of project failure. Effective budgeting isn’t based on guesswork or a vendor’s optimistic projections. It requires a defensible financial model built on objective data.
This guide provides a framework to shift your IT spending from a high-risk expenditure to a predictable investment.
The High Stakes of IT Modernization Budgeting
As a technical leader, your role is to manage a budget while avoiding project failure statistics. The core challenge is the intersection of massive IT spending with high failure rates.
Global IT spending is projected to reach $5.61 trillion, an increase of 9.8% in a single year. This capital is being allocated to cloud migrations, AI, and legacy system overhauls, often without sufficient data to support the investment.
Navigating Vendor Promises and Technical Realities
Vendors may quote a standard range, such as $1.50 to $4.00 per line of code for a COBOL migration. This figure often omits the technical risks that can invalidate the initial estimate.
For example, COMP-3 decimal precision loss during COBOL migrations can cause silent data corruption. According to our research, this single issue is a contributing factor in the estimated 67% of COBOL migration project failures.
A budget cannot be based solely on a vendor’s per-line-of-code price. It must account for the financial impact of technical risks like data type mismatches.
Moving Beyond Hopeful Spending
The objective is to construct a financial plan grounded in data that can withstand scrutiny and vendor narratives. This requires answering several key questions:
- What is the calculated cost of failure? What is the financial impact if a project joins the 67% that fail?
- What are the latent technical complexities? Are there data type mismatches or other technical issues that are not being addressed in the initial scope?
- What are the projected long-term operational costs? What will the modernized system cost to run, maintain, and secure post-launch?
This guide introduces a framework to answer these questions. By moving from speculative spending to predictable financial models, you can more effectively manage modernization projects. For a deeper analysis of available modernization paths, see our guide on application modernization solutions.
The following sections provide the necessary information to build a budget that is both defensible and executable.
A Deconstructed Framework for Modernization Budgeting
A defensible budget is an interconnected financial model, not a single figure on a presentation slide. Many budgets fail because they treat scoping, vendor costs, and risk as discrete line items. Confidence in the budget is derived from understanding how a change in one area affects the others.
The process should be deconstructed into four connected stages: Technical Scoping, Vendor Cost Modeling, Risk and Contingency Planning, and Run-Rate Forecasting. Each component must be independently sound before being integrated into a comprehensive budget that can withstand review from executive leadership and engineering teams.
This structured process is designed to break the cycle of unchecked spending, optimistic assumptions, and high project failure rates. A data-driven plan is the most effective mitigation.
Grounding the plan in empirical data is the primary method for avoiding non-performing investments.
Building a budget that holds up under scrutiny requires a structured approach. The table below outlines the four core pillars, their objectives, and the critical actions for each. This serves as a blueprint for creating a financial model that accurately reflects the project’s technical reality.
Modernization Budget Pillars and Key Actions
| Pillar | Objective | Primary Action | Example Metric |
|---|---|---|---|
| Technical Scoping | Translate business goals into quantifiable technical units. | Deconstruct high-level requirements into a concrete bill of materials. | 1.2 million lines of COBOL to be migrated. |
| Vendor Cost Modeling | Validate vendor quotes against market data. | Use industry benchmarks to analyze proposals and require line-item justification. | $1.50 - $4.00 per line of code for COBOL migration. |
| Risk & Contingency | Replace generic buffers with a calculated, risk-adjusted fund. | Mathematically model the probability and impact of specific failure scenarios. | $8,000 contingency for a 20% probability of a $40,000 data migration delay. |
| Run-Rate Forecasting | Project the ongoing operational cost post-launch. | Model the Total Cost of Ownership (TCO) for 3-5 years, including new hires and licenses. | +15% increase in annual OpEx due to new SRE hires. |
Each pillar is dependent on the previous one. A flaw in the initial scope will invalidate vendor models, undermine risk calculations, and make run-rate forecasts inaccurate. A solid foundation is critical for the integrity of the entire budget.
Technical Scoping Beyond Business Goals
Budgets often become inaccurate at this stage. Vague objectives like “improve user experience” are insufficient for financial modeling. Your role is to translate business goals into specific technical metrics that can be costed.
For a legacy system overhaul, this requires granularity.
- Codebase Quantification: Instead of “migrate the mainframe,” specify “migrate 1.2 million lines of COBOL.”
- Data Volume Metrics: Instead of “move to the cloud,” specify “migrate 25 terabytes of structured and unstructured data.”
- API and Integration Points: Document all endpoints. “Modernize the backend” becomes “refactor 75 legacy APIs and build 40 new microservices.”
This level of detail forces the conversation from abstract concepts to a concrete bill of materials, which is the foundation for subsequent budget components, particularly vendor negotiations.
Vendor Cost Modeling and Benchmark Validation
With a detailed technical scope, you can begin to model vendor costs. A quote is insufficient without market data for validation. Industry benchmarks are necessary.
For instance, knowing that COBOL migrations typically cost between $1.50 and $4.00 per line of code provides an immediate validation check for any proposal. A quote of $0.75/LOC may indicate an underestimation of complexity. A quote of $7.00/LOC may suggest inflated pricing or the identification of a significant risk that you have not yet accounted for.
Your role is not just to collect quotes, but to interrogate them. Require vendors to break down their pricing. An inability to justify their costs against your detailed scope is a significant red flag.
Quantifying Risk and Building Contingency
Contingency planning is frequently misused in budgeting. Applying a generic 15% buffer is an estimate, not a calculation. A defensible contingency is calculated based on specific, identified risks. A structured method for this is to use a system to prioritize urgent tech investments that helps weigh these factors correctly.
Model potential failure scenarios quantitatively. For example:
- Risk: Data migration fails due to an unforeseen schema conflict.
- Probability: An estimated 20% probability based on system age and complexity.
- Impact: A failure would require an additional four weeks from two senior engineers, at a cost of $40,000.
- Contingency Allocation: Allocate 20% of $40,000, or $8,000, specifically for this risk.
By repeating this process for the top five to ten identified risks, your contingency fund becomes a calculated reserve tied to specific potential events, rather than an arbitrary buffer.
Forecasting the True Run-Rate
Finally, you must forecast the operational expenses after the project is completed. The project budget is a one-time capital expenditure, while the operational budget is a recurring expense.
While a new cloud-native application may have lower infrastructure costs, it may require new skills to maintain. This could include hiring Site Reliability Engineers (SREs) or DevOps engineers. There may also be new licensing costs for tools like Datadog or New Relic. These are permanent increases to your annual operational spend.
A credible budget projects the Total Cost of Ownership (TCO) for a minimum of three to five years post-launch. This model must include new hires, training, licensing, and any consumption-based cloud costs. Failure to model this accurately means you haven’t reduced costs; you’ve shifted them, potentially to a higher, less predictable model.
Getting Granular: Line-Itemize Your Budget for Maximum Transparency
With a high-level framework established, the next step is to translate it into a line-item budget where every dollar is allocated. This is where financial strategy meets operational reality.
A vague budget invites scope creep and inflated vendor quotes. Proper budgeting for it modernization requires deconstructing all costs into auditable line items, eliminating ambiguous or “miscellaneous” categories.
This is not merely an accounting exercise. It is about building a financial document that is transparent and credible to both executive leadership and your engineering team. A detailed breakdown forces critical conversations to happen early, mitigating the risk of major financial variances later in the project.
Deconstructing Implementation Costs
Implementation typically represents the largest portion of the initial spend and is where hidden costs are most likely to occur. The most effective defense is to require a fully itemized Statement of Work (SOW) from any vendor under consideration.
A robust implementation budget must detail:
- Vendor Professional Services: Do not accept a single lump sum. Require a breakdown by role (e.g., Senior Engineer, Project Manager), hourly rate, and allocated hours per project milestone.
- Software Licensing and Subscriptions: Itemize every new license required, from core platforms to supporting tools. Specify the cost per seat or instance and the subscription term.
- Infrastructure Provisioning: Whether on-premises or cloud-based, detail the costs for servers, storage, and networking specific to the development and staging environments.
Scrutinize any line item labeled “Miscellaneous” or “Contingency” within a vendor’s SOW. These can be used to obscure profit margins or buffer against their own planning deficiencies. Your contingency fund should be managed by you, not the vendor.
Allocating for Rigorous Testing
Underfunding the testing phase is a common error that directly contributes to project failure. A defect identified in QA costs a fraction of what it costs to remediate in production. The budget must reflect this economic reality.
Key line items for the testing phase include:
- Dedicated QA Resources: Factor in the cost of your internal QA team or a third-party testing service. Do not assume developers can manage all testing responsibilities.
- Test Environment Costs: Account for the infrastructure required to run a dedicated QA environment that mirrors production. This is a material cloud expense that is often overlooked.
- Tooling and Automation: Budget for performance testing tools (e.g., JMeter, LoadRunner) and any test automation platforms. These should be viewed as investments in efficiency, not just expenses.
To maintain control over spending, you must address issues like slow budget variance analysis. This enables near-real-time tracking of actual spend against the plan, which is critical during a high-burn phase like testing.
Budgeting for Cutover and Remediation
Go-live is not the end of the project. The cutover process and the immediate post-launch period are high-risk and require a dedicated budget.
Your budget must account for:
- Parallel Run Costs: If you plan to run the legacy and new systems concurrently, you must budget for the duplicated infrastructure and operational overhead. This can double your run-rate costs for that period.
- Rollback Planning: A failed cutover is a tangible risk. Your budget should include the hours required to execute a rollback plan, which is often a significant effort.
- Post-Launch Hypercare: Allocate funds for a “hypercare” period, typically 2-4 weeks post-launch. This retains key vendor and internal personnel on standby to address immediate issues and is often priced as a separate retainer.
- Remediation and Bug-Fix Retainer: After the hypercare period, new defects will still be discovered. Budget for a bug-fix retainer with your implementation partner for at least the first six months. Be aware of vendors who reclassify bug fixes as “change orders” to increase revenue.
Building the Business Case for Your Stakeholders
You have constructed a data-driven, defensible budget. The next challenge is securing approval.
Securing the budget for a major modernization project is primarily a communication challenge. The calculated figures are ineffective unless they convince both executive leadership and your engineering team. These two groups have different priorities and require different communication strategies. You must be able to translate the same financial data into two distinct narratives.
Your task is to present the same set of numbers in two ways. For leadership, it is a narrative of risk and opportunity. For your engineers, it is a narrative of empowerment and realistic execution.
Pitching the Boardroom: Risk, Cost, and Competitive Edge
When presenting to executive leadership, focus on three key areas: risk, cost, and competitive advantage. Frame your entire pitch around these pillars.
The term “technical debt” is often ineffective with a financial audience. “Unmitigated financial risk” is more likely to command attention.
Do not say: “Our legacy COBOL system is getting hard to maintain.”
Instead, say: “Our current system carries a $1.2M annual operational risk due to talent scarcity. We also have a 35% higher probability of critical downtime during peak season, which would result in a material revenue loss.”
Use this checklist to construct your executive narrative:
- Translate Technical Debt into Financial Risk: Quantify the cost of inaction. This includes not just maintenance but also potential revenue lost during outages, the rising cost of hiring scarce COBOL talent, and potential compliance fines from running unsupported software. Our guide on how to calculate technical debt provides a framework for this.
- Frame Modernization as a Competitive Advantage: Explain how the project helps the business achieve its goals. Use business metrics, such as “reduce time-to-market for new features by 40%” or “unlock new revenue streams by integrating with modern payment APIs.”
- Present ROI & TCO Analysis: Provide a clear, five-year Total Cost of Ownership (TCO) analysis comparing the legacy system to the proposed modernized system. Be conservative in your assumptions and prepared to defend every number in your Return on Investment (ROI) calculation.
To the board, your $500K contingency fund is not “extra money”; it is “Calculated Risk Mitigation.” It represents a specific buffer allocated against identified project risks, such as a potential 15% data migration delay. This demonstrates prudent capital management, not just optimistic engineering.
Rallying Your Engineering Team: Resources and Realism
Your conversation with your engineering team will use the same budget numbers but for different purposes. Engineers are typically motivated by solving complex problems effectively and avoiding the burnout associated with maintaining outdated systems. They are often skeptical of unrealistic deadlines and under-resourced mandates.
Your business case for them is about enabling project success.
- Justify the Tooling: Frame the budget for CI/CD pipelines, automated testing, and observability platforms as an investment in developer productivity and system stability. It is a tangible commitment to reducing operational toil and emergency escalations.
- Defend Realistic Timelines: Point to budget allocations for proper testing cycles, performance tuning, and documentation as evidence that you respect the engineering process and are not driven solely by an arbitrary deadline.
- Position Contingency as a Sanity Buffer: The contingency fund is not for poor planning; it is a buffer for unforeseen technical challenges. It is the budget that acknowledges the reality that complex projects will uncover undocumented complexities.
To your engineers, that same $500K is the “Technical Debt and Discovery Buffer.” It is the funding that allows them to refactor a brittle module they discover, rather than implementing a temporary hack. It provides the necessary resources to solve problems correctly, preventing the creation of new technical debt.
By tailoring your message, you build credibility with both audiences. The board sees a strategic leader managing risk, while your engineers see a manager who understands what is required to build reliable software. This approach helps secure the budget and provides the team with the resources needed to succeed.
When to Pull the Plug on a Modernization Project
The most critical financial tool is the discipline to terminate a non-viable project. Budgeting for IT modernization involves not only securing funding but also knowing when to stop an initiative that no longer has a positive business case.
We are currently in an IT spending supercycle. IDC projects a 14% overall growth, with a 16% surge in the first quarter of this year alone. This creates pressure to modernize quickly.
However, with an estimated 67% of migrations failing and costs ranging from $1.50 to $4.00 per LOC, the pressure to continue a failing project can be significant. Canceling a project is not an admission of failure; it is a strategic decision to prevent a major capital loss.
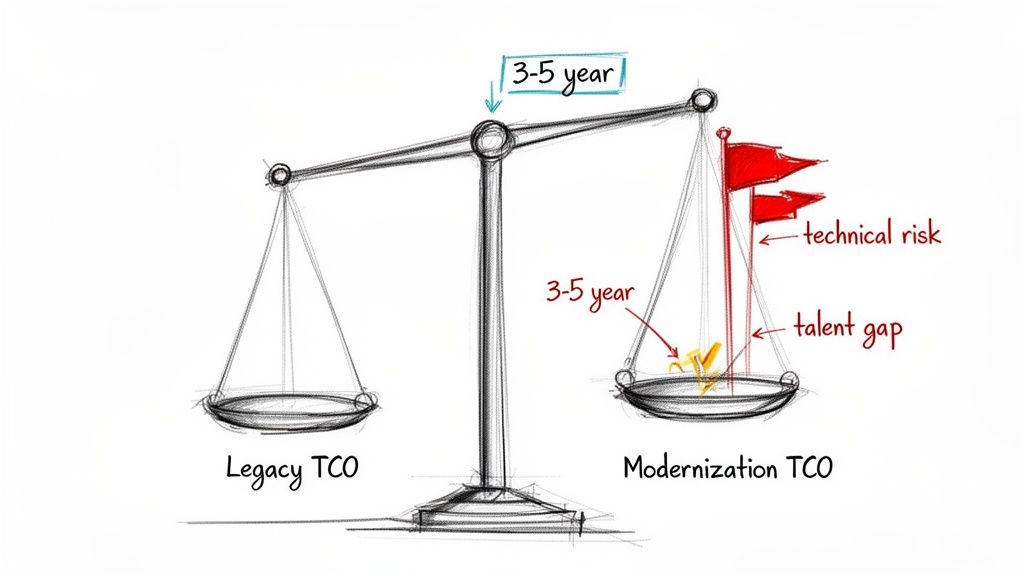
The TCO Inversion Point
The primary financial trigger for cancellation is a negative Total Cost of Ownership (TCO) projection. If your updated forecast shows that the five-year TCO of the new system will be higher than maintaining the legacy one, the business case is no longer valid.
This “TCO inversion” typically occurs for one of two reasons:
- Runaway Implementation Costs: The initial budget was based on faulty assumptions. Revised vendor quotes or escalating internal costs have eliminated the possibility of a positive ROI.
- Underestimated Run-Rate: The operational costs of the new technology stack—including specialist hires, complex cloud billing, and new software licenses—are significantly higher than originally modeled.
When the financial model no longer supports the project’s objectives, it is necessary to halt the initiative. If the five-year TCO for modernization is $4.2M, while maintaining the legacy system is $3.5M over the same period, you no longer have a business case.
Unacceptable Technical and Talent Risk
Sometimes the primary issue is not financial. A project may become technically or logistically infeasible regardless of funding.
Monitor these non-financial red flags:
- Unmanageable Technical Risk: The team discovers a fundamental architectural flaw that cannot be engineered around. This could range from data integrity issues, like the COMP-3 decimal problem in COBOL migrations, to a dependency on a technology nearing its end-of-life.
- The Talent Chasm: The project requires expertise in a niche technology, and the available talent pool is either nonexistent or prohibitively expensive. If you cannot staff the project for development and long-term maintenance, it is not viable.
A project may appear viable on paper, but if you cannot quantify and mitigate technical risks or secure the necessary talent, proceeding is a high-risk gamble. The decision to stop a project under these circumstances is a critical leadership function that protects the organization from a costly and protracted failure.
Your Toughest IT Budgeting Questions, Answered
Even with a robust framework, specific challenges will arise during budget planning. A small incorrect assumption can undermine an entire financial model. Here are data-driven answers to common questions that challenge technical leaders.
How Do I Handle Unexpected Scope Creep?
Scope creep is not a risk; it is an eventuality. The objective is not to prevent it, but to manage it with financial discipline.
When a stakeholder requests a “small new feature” mid-project, do not simply add it to the backlog. Immediately model its full cost impact.
This calculation must go beyond developer hours:
- Extended Timelines: Calculate the additional weeks of developer, QA, and project management time required. Quantify the dollar value of this delay.
- Increased Testing Overhead: Determine the cost of new test cases, additional QA cycles, and potential infrastructure changes.
- Long-Term Run-Rate: Analyze if the new feature increases the annual operational budget through new licensing, support, or maintenance costs.
Package these figures into a formal change request. This action transforms an informal request into a formal business decision, forcing the stakeholder to confront the true cost of their request.
How Do I Justify a Large Contingency Fund?
Finance teams are trained to view contingency as discretionary spending. Your task is to reframe it as a calculated, risk-adjusted financial instrument. The most effective way to do this is to tie every dollar to a specific, quantified risk.
Do not request a 15% contingency fund. Instead, present a risk register: “We require a $500K risk fund. This is allocated as follows: $200K against the 40% probability of a data migration delay; $150K for the 30% probability that specialist database performance tuning will be required post-launch; and $150K to cover the 25% risk of our third-party API integrations failing initial stress tests.”
This approach shifts the conversation from “Why do you need extra money?” to “Have we correctly priced these known risks?” It demonstrates rigorous planning and is more difficult to refute than a generic percentage.
How Can I Accurately Estimate Long-Term Operational Costs?
A frequent error in project budgeting is to neglect the ongoing costs of maintaining a system. Forecasting the true run-rate, or Total Cost of Ownership (TCO), is critical. The assumption that “moving to the cloud saves money” can obscure a significant increase in operational spending.
To build a realistic forecast, model costs for at least three to five years post-launch.
Include line items for:
- Specialized Talent: Your new stack may require hiring Site Reliability Engineers (SREs) or cloud security specialists, whose salaries are often 15-25% higher than traditional roles.
- Consumption-Based Cloud Services: Model cloud spend based on projected usage, not just list prices. Always factor in data egress fees, which are a common source of budget overruns.
- Third-Party Licensing and Tooling: Sum the annual costs for observability platforms like Datadog or New Relic, new security tools, and other required software subscriptions.
Without modeling these ongoing expenses, you are providing stakeholders with an incomplete financial picture. An accurate TCO forecast is the best tool for setting realistic financial expectations and demonstrating the long-term value of the project.
Making the right decision on a multi-million dollar modernization project requires more than a well-structured budget; it demands unbiased market intelligence. Modernization Intel provides data on 200+ vendors, their actual costs, and their project failure rates, enabling you to build a budget that aligns with market reality. Get Your Vendor Shortlist.
Need help with your modernization project?
Get matched with vetted specialists who can help you modernize your APIs, migrate to Kubernetes, or transform legacy systems.
Browse Services